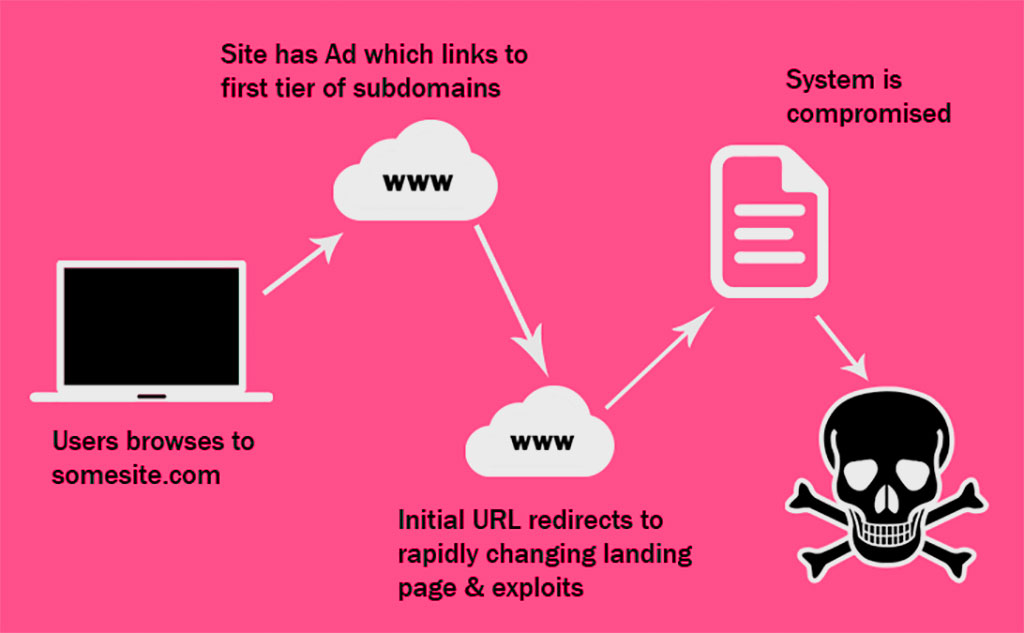
Cybersecurity researchers have uncovered a cunning cyberattack campaign that utilizes seemingly innocuous invoices to deliver a multi-stage malware attack. This deceptive tactic leverages phishing emails, which contain malicious Scalable Vector Graphics (SVG) file attachments. Upon opening the attachment, an intricate infection sequence unfolds, potentially unleashing a variety of malware strains onto the victim’s system.
Fortinet’s FortiGuard Labs, a leading cybersecurity research team, identified a range of malware deployed through this invoice-themed phishing scheme. These malicious payloads include Remote Access Trojans (RATs) such as Venom RAT, Remcos RAT, NanoCore RAT, and XWorm. Additionally, the attack arsenal incorporates a cryptocurrency wallet stealer, designed to pilfer digital currency holdings from unsuspecting users.
The attack’s complexity lies in its multi-layered approach. The SVG attachments themselves act as triggers, initiating the infection process once opened by the target. Further obfuscation techniques come into play with the extensive use of the BatCloak malware obfuscation engine. This tool, available for purchase by cybercriminals since late 2022, is a descendant of another obfuscation tool called Jlaive. BatCloak’s primary function is to mask the subsequent malware stages, allowing them to bypass conventional detection methods employed by security software.
ScrubCrypt, another layer in this elaborate attack, takes the obfuscated code a step further. It encrypts the malicious code, making it even more challenging for security systems to identify and prevent the infection. Once the obfuscated layers are peeled back, the malware payload typically arrives in the form of encoded batch scripts. These scripts then download and execute the final malicious program onto the compromised system.
The emergence of this multi-stage invoice phishing attack underscores the evolving tactics employed by cybercriminals. The attackers’ strategic use of readily available obfuscation tools and cryptocurrency-targeting malware highlights the increasing sophistication of these online threats. Security researchers emphasize the importance of user vigilance, particularly with regards to unsolicited email attachments, even those disguised as invoices or other seemingly legitimate documents. Furthermore, businesses are advised to implement robust security measures, including advanced email filtering systems and employee training programs focused on recognizing phishing attempts.
____________________________________
This article first appeared on The WIRE and is brought to you by Hyphen Digital Network
(The content powered by our AI models is produced through sophisticated algorithms, and while we strive for accuracy, it may occasionally contain a few minor issues. We appreciate your understanding that AI-generated content is an evolving technology, and we encourage users to provide feedback if any discrepancies are identified. As this feature is currently in beta testing, your insights play a crucial role in enhancing the overall quality and reliability of our service. We thank you for your collaboration and understanding as we work towards delivering an increasingly refined and accurate user experience.)
Also published on Medium.